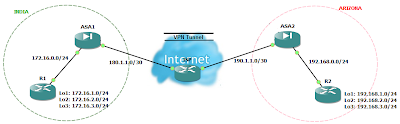
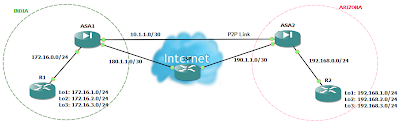
Fortigate Backup VPN
You can configure a route-based VPN that acts as a backup facility to another VPN. It is used only while your main VPN is out of service. This is desirable when the redundant VPN uses a more expensive facility.
You can configure a backup IPsec interface only in the CLI. The backup feature works only on interfaces with static addresses that have dead peer detection enabled. The monitor option creates a backup VPN for the specified phase 1 configuration. Redundant tunnels do not support Tunnel Mode or Manual Keys. You must use Interface Mode.
In the following example, backup_vpn is a backup for main_vpn.
You can configure a backup IPsec interface only in the CLI. The backup feature works only on interfaces with static addresses that have dead peer detection enabled. The monitor option creates a backup VPN for the specified phase 1 configuration. Redundant tunnels do not support Tunnel Mode or Manual Keys. You must use Interface Mode.
In the following example, backup_vpn is a backup for main_vpn.
config vpn ipsec phase1-interface
edit main_vpn
set dpd on
set interface port1
set nattraversal enable
set psksecret *****
set remote-gw 192.168.10.1
set type static
next
edit backup_vpn
set dpd on
set interface port2
set monitor main_vpn
set nattraversal enable
set psksecret *****
set remote-gw 192.168.10.1
set type static
end

Comments
Post a Comment