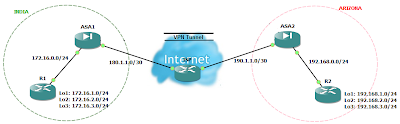
IPsec VPN as a Backup for Point-to-Point Link using IP SLA
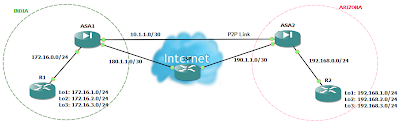
There may be times when you wish to access your remote site even when the point-to-point link (lease line) to that site is down. This is possible if you have also an internet connection to that site. You can configure an IPsec VPN between both the sites. But the problem is that even if you configure IPsec VPN on both the locations, the VPN will never come up when the point-to-point connection goes down. This is because even though that point-to-point connection is down, the interface status of firewall will always remain up due to devices of ISP in between and thus the static route will not let the incoming traffic to match the interesting traffic for IPsec VPN. So the solution to this problem is either to configure dynamic routing protocols or IP SLA. Cisco IP SLA monitor can be used to track the reachability of other location. Here is an example of such scenario using Cisco IP SLA monitor. If you need the gns3 lab for this or have any queries, you can leave your queries and email ID in comments.
ASA1
interface GigabitEthernet0
nameif P2P
security-level 50
ip address 10.1.1.1 255.255.255.252
!
interface GigabitEthernet1
nameif OUTSIDE
security-level 0
ip address 180.1.1.2 255.255.255.252
!
interface GigabitEthernet2
nameif INSIDE
security-level 100
ip address 172.16.0.2 255.255.255.0
!
access-list VPN extended permit ip 172.16.0.0 255.255.252.0 192.168.0.0 255.255.252.0
!
route P2P 192.168.0.0 255.255.252.0 10.1.1.2 1 track 1
!
sla monitor 1
type echo protocol ipIcmpEcho 10.1.1.2 interface P2P
num-packets 2
timeout 2000
frequency 3
sla monitor schedule 1 life forever start-time now
crypto ipsec ikev1 transform-set VPNTRANS esp-aes esp-sha-hmac
crypto map VPNMAP 1 match address VPN
crypto map VPNMAP 1 set peer 190.1.1.2
crypto map VPNMAP 1 set ikev1 transform-set VPNTRANS
crypto map VPNMAP interface OUTSIDE
crypto ikev1 enable OUTSIDE
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
track 1 rtr 1 reachability
!
tunnel-group 190.1.1.2 type ipsec-l2l
tunnel-group 190.1.1.2 ipsec-attributes
ikev1 pre-shared-key *****
ASA2
interface GigabitEthernet0
nameif P2P
security-level 50
ip address 10.1.1.2 255.255.255.252
!
interface GigabitEthernet1
nameif OUTSIDE
security-level 0
ip address 190.1.1.2 255.255.255.252
!
interface GigabitEthernet2
nameif INSIDE
security-level 100
ip address 192.168.0.2 255.255.255.0
!
access-list VPN extended permit ip 192.168.0.0 255.255.252.0 172.16.0.0 255.255.252.0
!
route P2P 172.16.0.0 255.255.252.0 10.1.1.1 1 track 1
!
sla monitor 1
type echo protocol ipIcmpEcho 10.1.1.1 interface P2P
timeout 2000
frequency 3
sla monitor schedule 1 life forever start-time now
crypto ipsec ikev1 transform-set VPNTRANS esp-aes esp-sha-hmac
crypto map VPNMAP 1 match address VPN
crypto map VPNMAP 1 set peer 180.1.1.2
crypto map VPNMAP 1 set ikev1 transform-set VPNTRANS
crypto map VPNMAP interface OUTSIDE
crypto ikev1 enable OUTSIDE
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
track 1 rtr 1 reachability
!
tunnel-group 180.1.1.2 type ipsec-l2l
tunnel-group 180.1.1.2 ipsec-attributes
ikev1 pre-shared-key *****
In the above configuration, as soon as the track object goes down, route towards the other ASA is removed from the routing table, resulting the incoming traffic from INSIDE interface to match the interesting traffic for IPsec VPN, followed by VPN tunnel creation.

Comments
Post a Comment