Anyconnect SSL-Client VPN with Self-signed Certificate on Cisco ASA
The Cisco AnyConnect Secure Mobility Solution provides a comprehensive, highly secure enterprise mobility solution. the Cisco AnyConnect Secure Mobility Solution continues to lead with next-generation security and encryption, including support for the Suite B set of cryptographic algorithms, and support for IPv6 networks. More importantly, it adapts its tunneling protocol to the most efficient method.
In the present scenario, we have to configure Anyconnect SSL remote access VPN for Sales department and Engineering department of a company. Engineering users will have to be provided with access to web server as well as FTP server, while sales users may only have access to the web server.
Anyconnect client authenticates the VPN gateway by it's Identity Certificate, so now we'll generate crypto rsa key to be used in enrolling for Self-Signed Identity Certificate followed by certificate enrollment.
Copy Anyconnect client image to the security appliance, which will enable the remote users to download and install the Anyconnect client software to their system when they connect to VPN Gateway from their web browsers.
And now we will do the rest of the configuration required for Anyconnect SSL VPN.
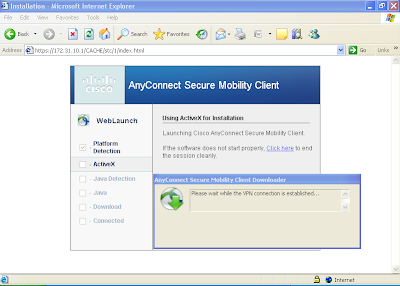
Now the remote users will be able to connect to the VPN . Remote users have to open the URL https://172.31.10.1 from their web-browsers to download and install the Anyconnect client software from the VPN gateway. Remote users will see the below screen when they will connect to VPN Gateway from their web browsers.
To Verify the connected users, use the following command.
To manually disconnect remote access VPN user, following command can be used
In the present scenario, we have to configure Anyconnect SSL remote access VPN for Sales department and Engineering department of a company. Engineering users will have to be provided with access to web server as well as FTP server, while sales users may only have access to the web server.
Anyconnect client authenticates the VPN gateway by it's Identity Certificate, so now we'll generate crypto rsa key to be used in enrolling for Self-Signed Identity Certificate followed by certificate enrollment.
crypto key generate rsa label VPNKeyPair
!
crypto ca trustpoint LocalTrust
enrollment self
fqdn ravpn.pacificgroup.co.in
subject-name CN=ravpn.pacificgroup.co.in
keypair VPNKeyPair
crypto ca enroll LocalTrust noconfirm
Copy Anyconnect client image to the security appliance, which will enable the remote users to download and install the Anyconnect client software to their system when they connect to VPN Gateway from their web browsers.
copy tftp://192.168.100.10/anyconnect-win-3.1.04059-k9.pkg flash:
And now we will do the rest of the configuration required for Anyconnect SSL VPN.
ip local pool RA_VPN_IP_POOL 10.10.20.1-10.10.20.255 mask 255.255.255.0
!
access-list RA_VPN_SplitTunnelACL standard permit 192.168.100.0 255.255.255.0
!
access-list SALES_VPN_ACL extended permit tcp any host 192.168.100.10 eq www
access-list SALES_VPN_ACL extended permit udp any host 192.168.100.10 eq domain
access-list ENGR_VPN_ACL extended permit tcp any host 192.168.100.10 eq www
access-list ENGR_VPN_ACL extended permit tcp any host 192.168.100.10 eq ftp
access-list ENGR_VPN_ACL extended permit udp any host 192.168.100.10 eq domain
!
!
ssl trust-point LocalTrust OUTSIDE
!
webvpn
enable OUTSIDE
anyconnect image disk0:/anyconnect-win-3.1.04059-k9.pkg 1
anyconnect enable
tunnel-group-list enable
!
!
group-policy GRP_SALES_SSL_RA_VPN internal
group-policy GRP_SALES_SSL_RA_VPN attributes
dns-server value 192.168.100.10
vpn-filter value SALES_VPN_ACL
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value RA_VPN_SplitTunnelACL
!
group-policy GRP_ENGR_SSL_RA_VPN internal
group-policy GRP_ENGR_SSL_RA_VPN attributes
dns-server value 192.168.100.10
vpn-filter value ENGR_VPN_ACL
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value RA_VPN_SplitTunnelACL
!
!
username salesuser password uXUrGApVTzN8lH14 encrypted
username salesuser attributes
vpn-group-policy GRP_SALES_SSL_RA_VPN
service-type remote-access
!
username engruser password osgMkcb3N.VlT8/u encrypted
username engruser attributes
vpn-group-policy GRP_ENGR_SSL_RA_VPN
service-type remote-access
!
!
tunnel-group SSL_RA_VPN type remote-access
tunnel-group SSL_RA_VPN general-attributes
address-pool RA_VPN_IP_POOL
tunnel-group SSL_RA_VPN webvpn-attributes
group-alias SSL_RA_VPN enable
!
!
object network VPN_USERS
subnet 10.10.20.0 255.255.255.0
object network INSIDE_NETWORK
subnet 192.168.100.0 255.255.255.0
!
nat (INSIDE,OUTSIDE) source static INSIDE_NETWORK INSIDE_NETWORK destination static VPN_USERS VPN_USERS
Now the remote users will be able to connect to the VPN . Remote users have to open the URL https://172.31.10.1 from their web-browsers to download and install the Anyconnect client software from the VPN gateway. Remote users will see the below screen when they will connect to VPN Gateway from their web browsers.
To Verify the connected users, use the following command.
ciscoasa# sh vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : engruser Index : 3
Assigned IP : 10.10.20.1 Public IP : 172.31.10.2
Protocol : AnyConnect-Parent SSL-Tunnel
License : AnyConnect Premium
Encryption : RC4 Hashing : none SHA1
Bytes Tx : 10062 Bytes Rx : 2536
Group Policy: GRP_ENGR_SSL_RA_VPN Tunnel Group: SSL_RA_VPN
Login Time : 13:12:04 UTC Tue Jul 16 2013
Duration : 0h:08m:39s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping: N/A VLAN : none
To manually disconnect remote access VPN user, following command can be used
ciscoasa# vpn-sessiondb logoff index 3
Do you want to logoff the VPN session(s)? [confirm]
INFO: Session with Index = 3 has been logged off

This comment has been removed by a blog administrator.
ReplyDeletethanks very easy to follow!
ReplyDelete