Cisco ASA Active/Active Failover Configuration
Active/Active failover is only available to security appliances in multiple context mode. In an Active/Active failover configuration, both security appliances can pass network traffic.
In Active/Active failover, you divide the security contexts on the security appliance into failover groups. A failover group is simply a logical group of one or more security contexts. You can create a maximum of two failover groups on the security appliance. The admin context is always a member of failover group 1. Any unassigned security contexts are also members of failover group 1 by default.
We have already seen the configuration for Active/Standby failover in the previous article. This article focuses on how to configure an Active/Active Failover configuration on ASA Security Appliance.
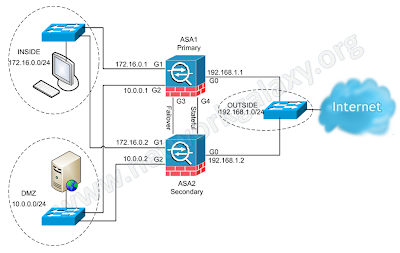
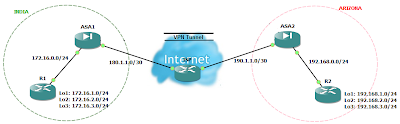
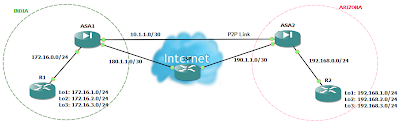
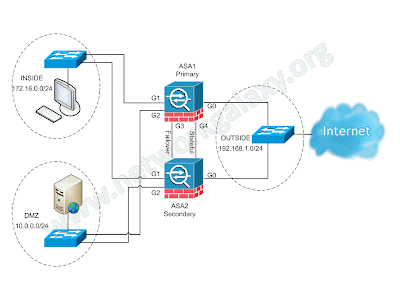
Network Diagram
(Physical Topology)
(Logical Topology)
You can download the GNS3 lab for this scenario from here
ASA Active-Active Failover.rar
Now let's dive into the configuration. To configure ASA Security Appliance for Active/Active Failover, first you need change the firewall mode to 'multiple' and configure contexts.
ASA1
! Enable auto generation of mac-address for shared physical interfaces
mac-address auto
! enable the physical interfaces
interface GigabitEthernet0
no shutdown
!
interface GigabitEthernet1
no shutdown
!
interface GigabitEthernet2
no shutdown
! Create and configure the contexts
context CTX-1
allocate-interface GigabitEthernet0
allocate-interface GigabitEthernet1
config-url disk0:/CTX-1
!
context CTX-2
allocate-interface GigabitEthernet0
allocate-interface GigabitEthernet2
config-url disk0:/CTX-2
Starting on the unit that will be the primary, and with multiple mode and context already in place.
ASA1
System
! Enable automatic assignment of private MAC address to each shared context interface
mac-address auto
! Create the first of the two failover groups
ASA1(config)# failover group 1
! Tell the failover system that the primary unit should be
! active for any contexts in this "failover group #1"
ASA1(config-fover-group)# primary
! Optionally, tell the system to take over the active role
! 2 minutes after a reboot by the primary unit for this group.
ASA1(config-fover-group)# preempt 120
! Do the same for failover group #2
ASA1(config)# failover group 2
! Tell the failover system that the secondary unit should be
! active for any contexts in this "failover group #2"
ASA1(config-fover-group)# secondary
! Request a preempt 2 minutes after reboot by the secondary unit for this group
ASA1(config-fover-group)# preempt 120
! By default all the contexts belongs to failover group 1.
! Tell the system that each of the contexts are assigned
! to 1 of the 2 failover groups
ASA1(config)# context CTX-1
ASA1(config-ctx)# join-failover-group 1
ASA1(config)# context CTX-2
ASA1(config-ctx)# join-failover-group 2
! Tell this physical box its "priority" or title (Primary or secondary).
! This priority (name) never changes for this physical unit
ASA1(config)# failover lan unit primary
! prepare the failover interfaces (the LAN fail and stateful link)
ASA1(config)# interface GigabitEthernet3
ASA1(config-if)# no shutdown
ASA1(config)# interface GigabitEthernet4
ASA1(config-if)# no shutdown
! configure the names and IP addresses for the 2 failover connections
ASA1(config)# failover lan interface LAN_FAIL GigabitEthernet3
ASA1(config)# failover link LINK_FAIL GigabitEthernet4
ASA1(config)# failover interface ip LAN_FAIL 10.1.1.1 255.255.255.252 standby 10.1.1.2
ASA1(config)# failover interface ip LINK_FAIL 10.2.2.1 255.255.255.252 standby 10.2.2.2
! set the prompt to include which context (if any) we are working in.
! Currently we are in the "system" (top level) configuration area.
prompt hostname context
CTX-1
! change from the system execution space to the context CTX-1 in order to add the standby addresses
changeto context CTX-1
! Configure context interfacees
interface GigabitEthernet0
nameif OUTSIDE
security-level 0
ip address 192.168.1.1 255.255.255.0 standby 192.168.1.2
!
interface GigabitEthernet1
nameif INSIDE
security-level 100
ip address 172.16.0.1 255.255.255.0 standby 172.16.0.2! Configure a default route for outgoing traffic
route OUTSIDE 0.0.0.0 0.0.0.0 192.168.1.10 1
CTX-2
! Change from CTX-1 and move to the context of CTX-2 in order to do the interfac configuration of that virtual firewall
changeto context CTX-2
interface GigabitEthernet0
nameif OUTSIDE
security-level 0
ip address 192.168.1.11 255.255.255.0 standby 192.168.1.12
!
interface GigabitEthernet2
nameif DMZ
security-level 50
ip address 10.0.0.1 255.255.255.0 standby 10.0.0.
! Configure a default route for outgoing traffic
route OUTSIDE 0.0.0.0 0.0.0.0 192.168.1.10 1
System
!move back to the system execution space
changeto system
!turn on the failover
failover
! save the system config, and all the context individual configs at the same time
write memory all
ASA1 is now seeing if there is an active failover devices for the 2 groups and when it see's that there isn't one, it will go active for both groups.
Moving over to Physical ASA2
ASA2
! Change the firewall mode to 'muultiple'
CiscoASA(config)# mode multiple
! tell this ASA what priority (title) it will have, primary or secondary
ASA2(config)# failover lan unit secondary
! Make sure the failover interface is up
interface GigabitEthernet3
no shutdown
! define the failover interface name and IPs
ASA2(config)# failover lan interface LAN_FAIL GigabitEthernet3
ASA2(config)# failover interface ip LAN_FAIL 10.1.1.1 255.255.255.252 standby 10.1.1.2
! turn on the failover
failover


Hi Prashant,
ReplyDeleteReally informative post. I recently cleared my CCNA Securitytest and there i read about this term, prior i had no idea what this is all about till i read this post...now atleast i know that it is sort of same as HSRP/VRRP/GLBP (mainly in term of failover) functinality in ASA.
Thanks!
IN THE SECOND FIREWALL, you would need to put failover lan unit secondary
ReplyDeleteAlso ts not failover link , should be failover lan interface.I guess you mistyped it
Thanks Ashwin for reporting the typo error. Now it's been corrected.
ReplyDeleteHI,
ReplyDeleteWhy Cant ping from DMZ to INSIDE network?